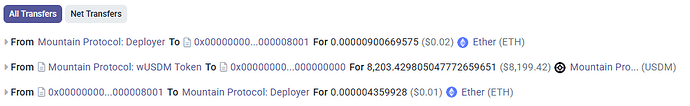Overview
On February 27th, 2024, a donation attack was performed on the Mountain’s WUSDM Exchange Rate Oracle that affected Venus and other protocols on zkSync. Venus ZKSync market suffered $902K of bad debt and has successfully recovered $185K bringing the total cost of the attack to $716K. This post provides a detailed technical post-mortem analysis of the type of attack executed and assessing the damage and bad debt caused by it.
Timeline
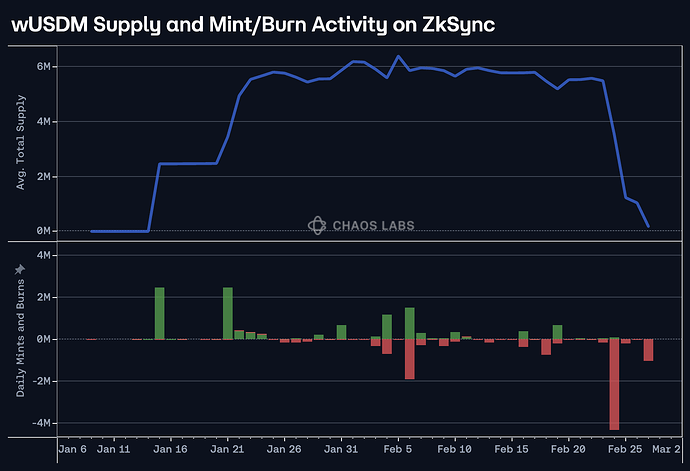
- At 3:15 PM of Feb 24th, the supply of wUSDM on ZKSync dropped from 5.33M to 1.27M following the redeem in this transaction.
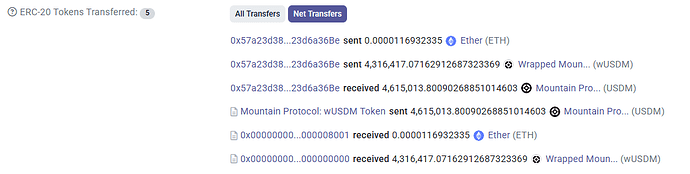
- At 3:45 AM of Feb 27th, the attack was performed in this transaction, where the user 45430c profited 86.72 ETH from manipulating the USDM exchange rate contract.
- Following the exchange rate dislocation, arbitrageurs bought wUSDM from the market in order to redeem it at a higher rate.
- At 1:41 PM on Feb 27th, Venus paused the wUSDM market
- At 3:24 PM Mountain Protocol manually set the exchange rate of wUSDM back to 1.067 by burning 8,203 USDM in the wUSDM contract
- At 3:33 PM Venus set the Collateral Factor of wUSDM to 0 and Reserve Factor to 100% in order to minimize new debt being generated
Attacker Flow
In order to explain the cause of the attack we cover the steps performed within the transaction that caused the exchange rate dislocation:
- The user 45430C, through the malicious contract deployed at be3506, took a flash loan from Aave for 2,100 WETH
- Deposited those 2,100 WETH on Venus as collateral in order to borrow 466,000 wUSDM on the be3506 wallet
- Transferred wUSDM from be3506 to its second wallet EC0561
- Supplied the wUSDM to Venus as collateral on the EC0561 wallet
- Repeated steps 2-4 for a total borrow of 2,167,431 wUSDM Debt and Collateral
- Borrowed an additional 411,021 wUSDM held in be3506
- Borrowed WETH from Venus against the wUSDM collateral on the EC0561 wallet for a total of 527.57 WETH
- Redeemed 411,021.57 wUSDM for 439,560.48 USDM at the original exchange rate of 1.0694
- Transferred 439,560.48 USDM to the wUSDM contract in order to inflate the exchange rate of wUSDM to 1.76413937
- The increase in exchange rate caused the be3506 wallet, holding WETH collateral and wUSDM debt, to be eligible for liquidation
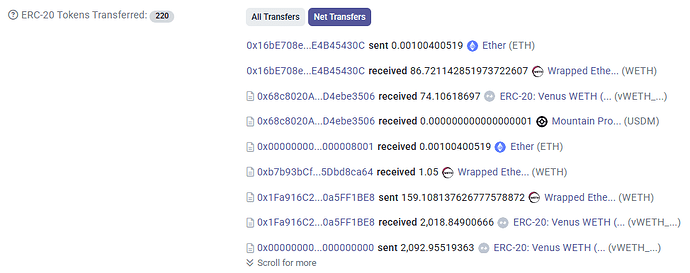
- Liquidated the be3506 by paying back a total of 1,882,000 wUSDM to obtain 1493.05 vWETH
- To perform the liquidation, he withdrew 1,882,000 wUSDM from Venus on the EC0561 wallet, hence being left with 285,431 wUSDM collateral
- During the liquidation, Venus Treasury accrued 71.34 WETH from the Liquidation Fees
- Withdraw 1498.08 WETH from the vWETH obtained through the liquidation
- Borrowed an additional 162.13 WETH against the remaining wUSDM collateral
- Paid back the Aave flash loan for 2101.05 ETH
- Profited 86.72 WETH and 55,000 wUSDM from the attack
ERC-4626 Vulnerability
ERC-4626, while designed for vault tokenization, does not include safeguards against manipulated exchange rates when used in lending protocols. The vulnerability arose from donation-based attacks, where an attacker artificially inflates the exchange rate by contributing assets without receiving new shares. This exploit disrupted all markets relying on USDM’s price oracle, particularly Venus and SyncSwap LPs.
Key Findings:
- ERC-4626’s
convertToAssetsfunction is insufficient ****within lending applications without external guardrails and restrictions. - The standard assumes that exchange rate calculations represent the underlying fundamental asset valuation but does not account for unverified external donations.
- wUSDM’s exchange rate oracle was directly used for lending, making it vulnerable to artificial inflation.
- This vulnerability was previously disclosed to Mountain Protocol; however, it was not shared in diligence during the Venus listing.
- The vulnerability was exacerbated by deriving the exchange rate in isolation on a per-chain basis, issued by Mountain, rather than leveraging a bridging solution that could have assigned a higher nominal value to USDM.
Discrepancy of USDM Exchange Rate on zkSync Implementation
The rewardMultiplier, and consequently convertToAssets, is expected to remain consistent across all chains, reflecting the underlying rebased yield source of wUSDM, which is the SOFR. Currently, this value returns 1072519. However, due to the identified vulnerability, the convertToAssets value within the wUSDM contract on ZkSync deviated significantly, rising to 1.764139, while it remained stable across all other chains.
Attack Rationale
Mountain Protocol’s native exchange rate mechanism varies across chains. On ZkSync, the wUSDM supply contracted to 1M on February 24th following a 4M burn from the chain, as illustrated below.
Following this drastic supply decrease, it was profitable for the attacker to:
- Borrow as much wUSDM as the Venus market allowed against a WETH flash loan
- Use it as collateral on a second wallet in order to borrow WETH
- Burn some of the
sharesof wUSDM borrowed and transfer USDMassetsto the wrapping contract to inflate the price - Use the inflated exchange rate to borrow more assets on Venus and liquidate one of the two accounts created
To mitigate this attack vector, the wUSDM contracts could have used a cross-chain exchange rate oracle, or, following proper disclosure, Venus would have implemented security measures to limit the appreciation of the exchange rate.
Broader Market Impact
As a result of this attack, two phenomena occurred:
-
All wUSDM collateralized debt positions on Venus were thus overinflated with respect to the exchange rate.
-
wUSDM’s outstanding supply shrunk down to <10K following the event as a result of the overinflated exchange rate and cross-chain arbitrage associated with the real exchange rate. This was technically performed through burning wUSDM for USDM, with the donation attack ultimately gifting such users an additional 439,560.48 USDM, distributed pro-rata to all wUSDM holders, external to the Venus Protocol.
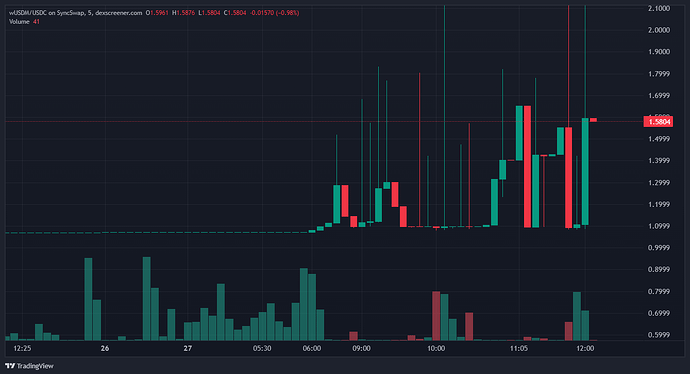
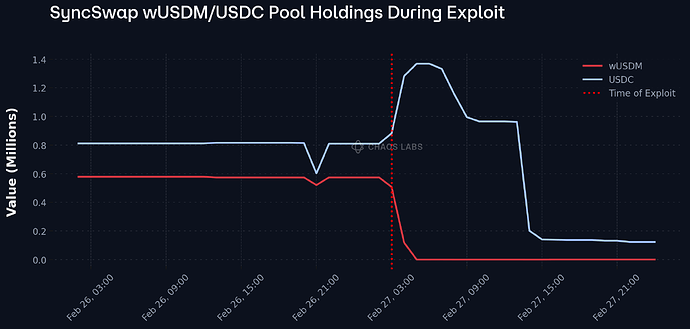
Consequently, SyncSwap LPs in the wUSDM/USDC pool were immediately arbitraged in line with the new exchange rate, allowing wUSDM holders to claim 1.78 USDM per unit. This led to 575K wUSDM being obtained from the pool and subsequently redeemed for USDM, leaving the pool with USDC, as illustrated in the plot below.
Following the attack, some other users used their supplied wUSDM assets to borrow Stablecoins or WETH. Thanks to the limited liquidity available and the LT of wUSDM, the additional loss caused by these wallets is limited, totaling $49.6K of additional bad debt.
Recovery
During the self liquidation process perform by the attacker, and during following liquidations performed on the remaining collateral on it’s wallet and one of the secondary market wallets, the Venus protocol accrued some liquidation fees that can be used to mitigate a portion of the bad debt created.
These funds are represented by 71.48 ETH and 11,942 wUSDM and can be used to mitigate the bad debt generated by the attack.
Security Measures Performed
After this attack occurred, the following security measures were performed:
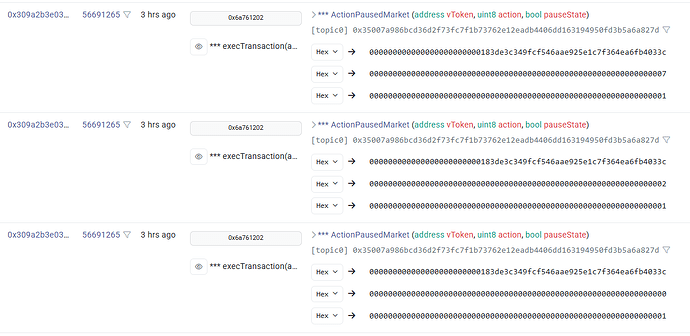
- Supply, Borrow, and Enter market operations were disabled
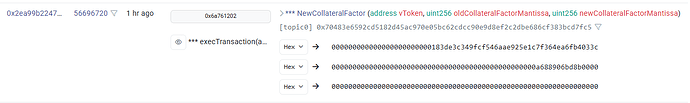
- Collateral Factor was set to 0, effectively disallowing existing users with wUSDM collateral to take advantage of the inflated exchange rate and borrow more capital
- Reserve Factor was set to 100%, making all bad debt growth entirely virtual
Shortly after this, the Mountain Protocol team reverted the exchange rate to factually reflect the previous value by burning 8,203 USDM supply to align with the aforementioned decreased supply. With a supply of just 10K, all relevant operations within the wUSDM market will remain paused indefinitely.
Reserve Factor and Utilization
Given the market’s current 100% utilization and the borrowing rate of over 70%, the main hacker position, holding a wUSDM bad debt, would accrue interest. However, thanks to the market’s Reserve Factor being set to 100%, any additional debt accrued gets returned to the Venus Protocol treasury once repaid.
Roughly $21K of the current $831K of bad debt is represented by virtually accrued debt.
Accounting
The following table represents the dollar values of the wallets interested and the cost to Venus in order to restore the health of the market:
| Account | Coll. Value | Coll. Asset | Debt Value | Debt Asset | Bad Debt |
|---|---|---|---|---|---|
| 0x4c0e4b3e6c5756fb31886a0a01079701ffec0561 | $297,245 | wUSDM | $318,190 | WETH | $20,945 |
| 0x68c8020a052d5061760e2abf5726d59d4ebe3506 | $0 | WETH | $831,547 | wUSDM | $831,547 |
| 0x924eded3d010b3f20009b872183eec48d0111265 | $53,086 | wUSDM | $73,858 | USDC,USDT | $20,772 |
| 0x2b379d8c90e02016658ad00ba2566f55e814c369 | $37,997 | wUSDM | $56,119 | USDC.e,USDT | $18,122 |
| 0xfffab9120d9df39eea07063f6465a0aa45a80c52 | $0.16 | wUSDM | 10,773 | USDC.e | $10,773 |
| Outstanding Bad Debt | $902,159 | ||||
| Liquidation Fees | $163,757 | ||||
| Virtual Bad Debt | $21,613 | ||||
| Net Loss | $716,789 |
Ongoing Effort
Since the time of the attack, Chaos Labs, in collaboration with the Venus team, made efforts to track and monitor the attacker’s funds and contacted Chainalysis and relevant authorities in order to freeze and retrieve the funds stolen by the attacker where possible.
Steps Forward
Chaos Labs is committed to ensuring a safe market for Venus users and has already performed a preliminary analysis of the existing assets on the platform to ensure that the attack cannot be replicated further both on this and other Venus markets.
However, continued monitoring of Venus’s assets will be performed in order to mitigate further risks of price manipulation.
Additionally, in light of this event, OpenZeppelin will be publishing new guidance on safe ERC-4626 integrations. Future implementations will require:
- Additional guardrails against donation attacks.
- Oracle refinements to prevent manipulations from altering loan calculations.
To further mitigate this attack vector, an upside-capped oracle setup—such as Aave’s CAPO mechanism—will be implemented for all yield-bearing assets, preventing manipulation through artificial yield spikes.